Norsk
Security, Emergency Preparedness and Data Protection at UiT
UiT The Arctic University of Norway processes large volumes of information relating to research, education, dissemination og administration. It is crucial that we attend to the information security in a proper manner, not least safeguarding the integrity that UiT is reliant on as a research and education institution. This shall occur irrespective of whether the processing in question is physical or digital.
Do you wish to contact the Privacy and Information Security Office? Please send an e-mail to security@uit.no
The Security, Emergency Preparedness and Data Protection Management System was adopted by the University Board on the 22nd of June 2023. This expanded UiTs Information Security and Privacy Management System which initially was adopted by the board in 2015 and later revised several times. Through this management system, UiT shall have a comprehensive approach so we can have governance and control of Security, Emergency Preparedness and Data Protection at the university.
The management system consists of three parts: governance, implementation and control. The University Board is responsible for amendments in the governance part (Chapters 1-2), while the Administrative Director has responsibility for amendments in the parts concerning implementation (chapters 3 - 12) and the Rector amends the parts regarding control (Chapters 13-15).
Chapter 1: Introduction and structure
[Adopted by the University Board on 22.6.23, case S 21/23]
Background
As the world’s northernmost university, UiT is strategically placed to develop and disseminate knowledge about the Arctic and the High North. UiT focuses on research and education about nature, society, technology, environment, culture, humans and the interaction between these. Our academic breadth and closeness to nature and society make UiT uniquely suited to contribute knowledge and competence to transformation and adaptation processes and future-oriented solutions across disciplines, trade and industry and civil society.
UiT has students and staff from different countries and places and collaborates with research and educational institutions at home and abroad, as well as with public and private actors.
UiT is a comprehensive university at the international forefront that, due to its location and research profile, may be particularly vulnerable to threats and attacks. Activists, criminals, and state intelligence seek to achieve financial gain, political goals or other advantages through manipulation, sabotage, and espionage. UiT's research data may be particularly vulnerable to physical or digital security breaches in the event of, for example, sabotage and/or espionage.
Purpose and intention
Through preventive security, UiT will reduce the probability of an undesirable incident occurring and reduce the consequences of such an incident. This work must be seen in the context of emergency preparedness, which does not prevent an undesirable incident from taking place, but includes planning prior to an incident, the actual handling when this either occurs or is imminent, and the subsequent recovery. Through good work with emergency preparedness, UiT will be able to increase the level of security at short notice.
UiT has an extensive amount of assets, information and infrastructure that must be protected and preserved, and this requires a systematic and coordinated approach to the work. This also includes proper safeguarding of values worthy of protection, good export control routines to prevent illegal transfer of knowledge and ensuring that international cooperation takes place in a prudent manner.
Measures that are necessary for security purposes may be invasive to employees, students and others affiliated with UiT. When assessing which, and how, security measures should be implemented, it is essential to simultaneously consider how privacy is affected and best safeguarded. Furthermore, UiT processes a large amount of personal data in all parts of its organization, and good compliance with data protection legislation is important to maintain trust among employees, students, research participants, partners and guests.
Appropriate and good management of these areas requires that they are seen in context rather than separately, and that the work is organized and established as a coherent service. This is a challenging exercise, but at the same time necessary for UIT to achieve a proper level of security, and good protection of privacy for everyone associated with UiT.
To succeed in this, UiT has established a common management system for security, emergency preparedness and data protection.
Scope and content of the management system
The main areas to be safeguarded through this management system are information security, civil protection, emergency preparedness, data protection, export control and national security. All of these areas intervene, and they encompass the physical, human, organizational and digital domains. All these domains can constitute a vulnerability that can be exploited consciously or unconsciously, by external or internal actors. In order to achieve an adequate level of security, UiT is dependent on seeing these in relation to each other and taking into account the interaction between these different areas and above-mentioned domains. For example, digital systems may be well secured in themselves, but if the physical security is weak and a dishonest actor gets into a data centre, a lot of damage can be done.
Societal developments and a changed threat and risk picture blur the distinction between civil protection and state security. The work of identifying and safeguarding values that are important for national security is complicated, partly because relevant measures for compliance with the Security Act and export control regulations may interfere with the core activities and potentially UiT's opportunity for fulfilling its social mandate as a research institution.
In today's higher education, there is a strong focus on learning-promoting technology and digital examination methods, and it is difficult to balance the need to frequently use new services while at the same time safeguarding information security and privacy/data protection. Both the Ministry of Education and Research and UiT have ambitious digitalization strategies, and fulfilling these while safeguarding information security and privacy is a demanding task.
Furthermore, UiT processes a large amount of personal data about employees, students, research participants and others. The regulations for legal handling of personal data are extensive and complex, and good guidelines, routines, tools and knowledge are required to ensure that UiT complies with relevant regulations in all processing of personal data.
In addition, major accidents can occur as a result of technical or human error, pandemics, supply failures or other disasters triggered by unintended events such as natural disasters, or intentional actions of those who want to harm us. Such events can be in the physical or digital space, or a combination. The incidents can be so varied in scope and type that it is challenging to build good emergency preparedness that allows UiT to respond quickly and adequately.
The establishment of a common management system will ensure that UiT has a planned and good handling of this complex field. Safeguarding security, emergency preparedness and data protection is a managerial responsibility, and this work shall be an integral part of overall corporate governance.
The management system for security, emergency preparedness and data protection at UiT includes
- Anyone1 who gets access to UiT's information assets
- All UiT study sites/campuses
- All organizational units
- All technology2
- All information assets3
- All critical national values (information, objects and infrastructure)
This management system does not include UiT's work within Health, Safety and Environment (HSE), which is regulated through its own internal control system. It is incumbent upon the university management to ensure good interaction between the management system and the HSE system.
------------------------------------------------------------------------------
1 Students, employees, guests, partners etc.
2 ICT systems, computer networks, databases/registers etc.
3 Information value is a collective term that includes both the information itself and associated support values such as ICT systems, digital services, computer equipment of various variants, etc.
Vision, goals and principles
UiT shall establish and maintain a sound security-culture, administration, management and safeguarding of its values in order to safeguard society's trust in the university's education, research and dissemination.
UiT shall:
- work targeted, systematic and risk-based with civil protection, information security, emergency preparedness and data protection
- take a comprehensive and common approach internally at UiT to this work
- reduce vulnerabilities to UiT's information assets
- include civil protection, emergency preparedness, information security and data protection in the university's decision-making processes
- simplify and improve the University's security, preparedness and data protection policies and processes
- improve the ability to detect and handle incidents, deviations and breaches quickly so that any consequences for the organisation are minimised
- provide training and awareness that enables managers, employees and students to prevent, detect and report incidents
- Include civil protection, emergency preparedness, information security and data protection as regular topics in management meetings and training
Risk management
UiT's risk picture is dynamic and will vary over time. It is therefore necessary to work systematically on risk management and acceptable risk. Effective risk management shall give students and staff the best possible basis for understanding how much risk UiT is willing to accept in the process of creating value. UiT has a risk-based approach to safeguarding security and emergency preparedness.
Risk management is central to good safeguarding of information security, data protection, civil protection, physical and personnel security, fire and emergency preparedness, and national security. Often, risk can be reduced to an acceptable level through measures, but in some cases the risk is too high for the projects in question, procurement of the desired systems, etc. This may be because there are no measures, or the measures are too costly to implement.
Risk assessment shall take place within the limits laid down in the management system, and there are some differences in how risk is assessed within the various areas, see Chapter 4. Carrying out risk assessments will depend on knowing which values are being processed, including how these are classified. See Chapter 3 for regulation and information on valuation and classification.
It is not possible to eliminate every risk, but UiT will work systematically and purposefully to have a risk level that is acceptable, seen in relation to UiT's goals and risk picture. UiT has set limits for acceptable risk within information security and civil protection.
Structure of the management system
The management system consists of three main elements (parts):
- Governing part – structure, vision and goals, risk management as well as roles, tasks and responsibilities
- Implementing part – specific policies and routines, including classification of information, risk and data protection impact assessment, fundamental security of the digital and physical domain, organizational and human measures.
- Controlling part – internal audit and control, reporting and handling of incidents and deviations, and management's review/annual report.
Chapter overview
| Chapter number | Chapter | |
| Governing part | 1 | Introduction and structure |
| 2 | Roles, responsibilities and tasks | |
| Implementing part | 3 | Classification and valuation |
| 4 | Risk and data protection impact assessments | |
| 5 | Physical security | |
| 6 | Digital security | |
| 7 | Personnel security | |
| 8 | Emergency Preparedness | |
| 9 | Procurement/maintenance/development | |
| 10 | Data protection / privacy | |
| 11 | ICT resources and users | |
| 12 | International cooperation and export control | |
| Controlling part | 13 | Internal control and audit |
| 14 | Handling of incidents and non-conformities | |
| 15 | Management Review/Annual Report |
Chapter 2: Roles, responsibilites and tasks
[Adopted by the University Board on 22.6.23, case S 21/23]
Safeguarding security, emergency preparedness and data protection is a managerial responsibility. The university management is responsible for setting the framework and closer premises and regulation of UiT's work in this area. The unit managers are responsible for ensuring that this is followed up in their unit, as well as establishing more detailed guidelines and routines within their area of responsibility if required, for example due to special activity.
This chapter describes the main features of UiT's organisation of the work within security, emergency preparedness and data protection. There are also responsibilities and tasks for other roles, but these are context-dependent and will then be stated in relevant regulations. For example, system owners according to the Quality System for IT, see chapter 6 – Digital security.
University board
- Processes and adopts the management system for security, emergency preparedness and data protection at UiT
- Supervises UiT's work within security, emergency preparedness and data protection
Rector
- Has overall responsibility for security, emergency preparedness and data protection at UiT
- Is responsible for preventive safety work, and that this work results in a proper level of security
- Responsible for allocating the necessary resources for adequate safeguarding of security, emergency preparedness and data protection
Administrative Director
- has the administrative responsibility for the management system for security, emergency preparedness and data protection, and shall ensure that it is implemented and maintained
- responsible for the organization of UiT's work on security, emergency preparedness and data protection, including the associated service
- exercises overall responsibility for all processing of personal data at UiT
- is a strategic leader in crisis situations, and heads the Central Preparedness Group (SBG)
- shall ensure that UiT has appropriate preparedness with regard to handling crises and accidents
- shall ensure that the rector is involved in the handling of incidents and deviations to the extent warranted by the nature of the case
- has coordinating responsibility for the regular meetings between The Norwegian Police Security Service (PST) and the university management, and is the contact point for PST if they want meetings with UiT beyond these
- is responsible for the preparation of the annual report for security, emergency preparedness and data protection
- appoints members of the group for overall assessment of Data Protection Impact Assessments (UiT's DPIA group)
Unit boards
- The unit boards refer to the faculty boards, the University Library Board and the board of the Arctic University Museum of Norway and the Academy of Fine Arts
- Supervises their unit's work within security, emergency preparedness and data protection
Heads of faculties and units
- Head of unit means the Dean, Library Director, Director of the Arctic University Museum of Norway and the Academy of Fine Arts, and the department directors in the joint administration.
- Responsible for ensuring that the unit
- comply with the requirements set by law, regulations and UiT's internal management system for security, emergency preparedness and data protection, including the performance of associated tasks
- prepares internal guidelines and routines if necessary to fulfil the requirements and perform the tasks in the above point
- allocates the necessary resources for adequate safeguarding of security, emergency preparedness and data protection within one’s area of responsibility and emergency preparedness, including that the unit has the appropriate expertise available
- Conducts and coordinates work on risk and vulnerability assessments (ROS) and emergency preparedness with local emergency preparedness groups at the location in question
- Shall ensure that incidents and non-conformities are followed up and closed, in accordance with UiT's internal guidelines.
- Shall ensure that employees, students and guests are informed of the routines and guidelines that apply at all times
- Shall ensure that employees and students are given the necessary training in the areas of security, emergency preparedness and data protection, and that these topics are integrated to a relevant extent in all internal training for which the unit is responsible
- Shall ensure compliance with requirements in central emergency preparedness plans related to training, ROS and exercises within its emergency preparedness area, and if the unit has a local emergency preparedness group, the unit manager must either lead this or be a member.
Units and others with special responsibilities and authority
Some units and others have special responsibility for parts of UiT's work within security, emergency preparedness and data protection. This applies to all departments in the joint administration as well as individual faculties.
Data Protection Officer
- reports directly to the leader of the rector's staff
- shall inform and advise UiT's employees and students about current obligations under data protection legislation
- shall monitor UiT's compliance with data protection legislation
- shall be involved at the right time and level in matters relating to data protection
- shall advise on the Data Protection Impact Assessment (DPIA) and monitor the implementation of these assessments
- shall be involved at an appropriate level in the handling of non-conformities pursuant to data protection legislation, and as a minimum be informed of the content and scope of non-conformities
- shall prepare an annual report to be submitted to the University Board
- have the right to attend and speak in UiT’s Information Security and Privacy Forum
- can be contacted directly by data subjects with questions about UiT's processing of their personal data, and about the exercise of their rights under the General Data Protection Regulation (GDPR)
- cannot be instructed on the performance of the duties of the Data Protection Officer pursuant to Article 39 of the General Data Protection Regulation (GDPR)
Special roles and responsibilities in research
Internal forums for security, emergency preparedness and data protection
Employees and students
- Have an obligation to
- familiarize themselves with and comply at all times with applicable law, regulations and UiT's internal regulations within security, emergency preparedness and data protection, including reviewing available information and training from UiT
- prevent and report nonconformities when they occur, including incidents that may involve non-conformities
Chapter 3: Classification of information and value assessment
This chapter has been updated. The Norwegian language version is the updated version. The English version will be updated, but until then only the Norwegian language version is valid.
Chapter 4: Risk Assessments and Data Protection Impact Assessments
This chapter has been updated. The Norwegian language version is the updated version. The English version will be updated, but until then only the Norwegian language version is valid.
Risk assessments are intended to reveal any undesirable incidents/threats that may lead to a breach of the information security at UiT. Consequently, the risk assessments have a central place in the work to ensure safe and secure processing of UiT’s information assets. In addition to revealing what can go wrong, the assessments shall reveal what we have done and what more we can do to prevent the occurrence of undesirable incidents and reduce the consequences of any incidents that do occur.
The risk assessment must be seen in the context of established risk acceptance criteria (cf. Section 2.3), and the acceptable risk must be determined before the risk assessment is conducted. If the risk of one or more undesirable incidents occurring is greater than what is defined as acceptable, this risk must be mitigated by implementing preventive measures.
Risk assessments must be conducted
- when the risk level changes
- prior to starting the processing of personal data
- at the start of research projects
- when establishing or changing ICT systems
- when organisational changes are made that may affect the information security
All risk assessments must be documented in writing. If risk assessments reveal matters requiring follow-up, someone must be named who is responsible for stipulating relevant measures and plans for the follow-up of these. The risk assessment shall be submitted to the Information Security Advisor(s) who shall utilise these in the management’s annual review and ensure that the documents are filed in UiT’s archival system.
Read more about risk assessments
Chapter 5: Physical Security
This chapter has been approved, however for the time being it's only available in Norwegian. It will be translated to English, and then posted here.
Chapter 6: Digital Security
Through the management system in general and this chapter in particular, UiT will ensure that security is safeguarded in all ICT systems, services and infrastructure. This chapter's target group is those at UiT who will procure, operate and/or manage ICT systems, services, units and infrastructure, and contain principles, guidelines and routines, etc. to be followed.
Regulations, guidelines and routines aimed at users of UiT's ICT resources, systems and services can be found in chapter 11 (ICT resources and users).
UiT's measures for cyber security are largely rooted in NSM's basic principles for ICT security and UiT's ICT regulations. Continuous efforts are made to improve the security of systems and services.
There are primarily three main groups of security measures:
1. System Security
As a guiding principle, all systems, services, servers and clients should follow security best practices. This means that
a. All systems shall run up-to-date software, and published security updates shall be installed within the given deadline.
b. Functionality that is not used shall be turned off.
c. Data shall be encrypted and secure protocols used.
d. All services available on the Internet shall have a security classification based on what information they contain and are approved for.
2. Authentication and multifactor requirements
As a main principle, anonymous access to systems, networks and services is not permitted. As a general rule, all authentication must take place via UiT's user management systems. Multifactor is a basic safety measure and should be used whenever possible. If this is not possible, this will either require further measures, or place strict restrictions on the type of data the system/service can be approved for.
Authentication and use of multifactor are further regulated by separate guidelines attached to this chapter.
3. Securing data
As a main principle, UiT's data shall be secured through adequate backup routines, and more detailed requirements (scope/retention period) shall as a rule be established through risk assessments (see chapter 4), in light of the requirements imposed on the integrity and accessibility of the data (see chapter 3 on classification and valuation). However, all data processed in central systems shall be subject to backup measures that ensure against unwanted alteration and deletion.
Operational safety and system management
System changes with consequences for vulnerability and access control, and technical security measures related to basic and/or important infrastructure, devices, systems and services at UiT must be reported to the Operational Security Team (OST). This includes the schedule for implementation of measures, as well as the status of their implementation. Such measures will typically be identified by the system owner through risk assessments or incidents, but it may also be measures that the OST identifies and decides should be implemented.
OST is also responsible for preparing and maintaining an overview of planned central technical safety measures and following up the progress of these measures throughout the year. This includes measures that the group itself identifies as necessary. The group can assign responsibility for the measures to the various units at UiT, depending on the topic. See also Chapter 2 for a description of the Operational Security Team.
Guidelines and procedures
<See Norwegian language version>
Chapter 7: Personnel Security
This chapter has been approved, however for the time being it's only available in Norwegian. It will be translated to English, and then posted here.
Chapter 8: Emergency preparedness
This chapter has been approved, however for the time being it's only available in Norwegian. It will be translated to English, and then posted here.
Chapter 9: Procurement/maintenance/development
This chapter has been approved, however for the time being it's only available in Norwegian. It will be translated to English, and then posted here.
Chapter 10: Data Protection / Privacy
Privacy is an important human right that, among other things, must safeguard the individual's personal integrity and privacy. The term encompasses not only the protection of privacy and personal integrity, but also the right of individuals to influence how their own information is used and disseminated. There are several different regulations to take care of this, but the most comprehensive and fundamental are the Personal Data Act and the General Data Protection Regulation ("GDPR") which regulates the use of personal data. Examples of other relevant legislation are the Health Research Act and the Personal Health Data Filing System Act with regulations, the Working Environment Act with regulations and a number of other special legislation. Often these apply in addition to GDPR.
UiT processes an extensive amount of personal data, in all parts of its business. See below under "key terms" for an explanation of what personal data is.
Safeguarding the information security of personal data is central, but there are also a number of other obligations. For example, one must have a legal basis (processing basis) for processing the information (e.g. consent, legal obligation, fulfilment of agreement, etc.), there are special considerations related to the reuse of information for new purposes and that individuals' rights must be safeguarded (such as duty of information, right of access, deletion etc).
UiT also processes personal data about vulnerable persons, and stricter requirements are imposed on the assessment of what is needed to do this legally.
If the processing involves a high risk for individuals, a data protection impact assessment (DPIA) must be carried out in addition to a risk assessment, see chapter 4 of the management system.
Through the management system in general and this chapter in particular, UiT shall ensure that all processing of personal data meets regulatory requirements and takes place in a prudent and trustworthy manner.
Key terms
The General Data Protection Regulation (GDPR) uses a number of terms, the most important of which are described here.
Use of Data Processors
There are a number of obligations that must be fulfilled when using data processors:
- If UiT is the data controller and use a data processor:
- There must be either a signed data processing agreement or other legal act binding for the data processor vis-à-vis UiT, which meets the requirements under the GDPR
- No personal data may be sent or made available to the data processor until the agreement or equivalent is in place
- Risk assessment shall be carried out to the extent required, see chapter 4.
- The data processor must be followed up to ensure that the obligations under the agreement are complied with.
- If UiT is a data processor for others:
- There must be a signed data processing agreement that meets the requirements under the GDPR
- It is the data controller's duty that such an agreement is in place, but UiT shall not receive or otherwise process personal data until this agreement has been signed
- Ensure that personal data from the various data controllers are kept sufficiently separate (separated) from each other and from UiT's own data, unless there are justifiable reasons why this is not required, and the GDPR is still complied with
- Ensure adequate information security for personal data processed on behalf of the client (data controller), in accordance with what is agreed in the data processing agreement.
Protocol of processing activities
UiT shall keep records of all processing activities involving personal data.
For activities where UiT is responsible for processing, this protocol is twofold:
- Research projects: protocol is maintained by Sikt data protection services on UiT's behalf (“Institution portal”, formerly “message archive”)
- All other activities: A unified protocol, and each unit maintains its part of the protocol. The units shall appoint a contact person who is made visible via uit.no/security.
In addition, a protocol must be kept of activities where UiT is the data processor. These are reported to the units' contact person.
Transfer to external parties and abroad
The transfer of personal data out of UiT encompasses more than that copies are sent to an external party or that data is stored in a data center at a data processor. Remote access (e.g. through support) is also considered a transfer, and this is especially important to bear in mind if the person or organization who is to have access is outside the EU/EEA. In the case of information that may be subject to export restrictions, this must be taken special account of and assessed specifically.
- Disclosure to external parties
If personal data is to be transferred to external parties (persons or businesses) who are not data processors, there must be a legal basis for this.
In many cases, the extradition is required by law (e.g. to the Norwegian State Educational Loan Fund, the Norwegian Tax Administration, requests for access pursuant to parts of the Freedom of Information Act, etc.). In cases where disclosure is not required by law, UiT shall ensure that the recipient has an adequate legal basis for its processing of personal data.
If the disclosure entails that the personal data is processed for new purposes, UiT must also consider whether this is permitted reuse under the GDPR.
- Transfer abroad
If personal data is to be transferred out of Norway, either to a data processor or other data controllers, there are different rules that apply depending on the country/region in question.
A distinction is made between transfers within the EU/EEA, and to countries outside the EU/EEA, as well as to international organizations. Within the EU/EEA, a separate transfer basis is not required, while the latter two cases require such a basis.
It is important to note here that
- This only refers to the requirement for a legal basis for the actual transfer of the information out of Norway and to another country/international organization. In addition, there must always be a legal basis for transferring to the recipient in question (e.g. a data processing agreement), regardless of whether the recipient is in Norway, within/outside the EU/EEA or is an international organization.
- Remote access from abroad (e.g. from user support) is also considered a transfer in this context
Guidelines, routines and guides
- Student Data Processing Policy [In Norwegian]
- Guidelines for the processing of personal data for UiT's personell [In Norwegian]
- Guidelines for the processing of personal data in research and student projects
- Routines for the use of private equipment when processing personal data in research and student projects [In Norwegian]
- Routines for health research [In Norwegian]
Chapter 11: ICT resources and users
Through the management system in general and this chapter in particular, UiT will ensure that security and data protection are safeguarded when UiT's ICT resources are used. Safeguarding safety is not possible without a good security culture, and this is built by everyone being familiar with, and aware of, their responsibilities.
This chapter's target group is all users of UiT's ICT resources (employees, students, guests and others). Regulations, guidelines and routines anchored in this chapter regulate how ICT resources are to be used, and what obligations and security measures users must follow, see below. UiT's ICT resources shall strengthen and support UiT's activities, and its use shall be in accordance with this. Systems and services should only be used for the type of data for which they are approved, see table below.
Regulations, guidelines and routines aimed at those who are to purchase, develop or manage ICT resources are found in chapter 6 (digital security).
Use approved systems and services
UiT has a number of systems and services that can and should be used for processing UiT's data. It is not permitted to process UiT's data in private services (such as the user's private/personal subscription to OneDrive, iCloud, Google Drive, DropBox, etc.).
However, not all of UiT's systems and services are approved for all types of data. In accordance with Chapter 3 of the management system, all information shall be classified according to requirements for confidentiality, integrity and availability. Risk assessments determine the level for which the various services and systems are approved, as well as any prerequisites for approval.
The Privacy and Information Security Office shall maintain a table of uit.no/security of services/systems that have been approved in accordance with Chapter 3. This is updated continuously as the system owner reports either new systems/services with associated approval level, or changes in approvals or prerequisites.
Regulations, guidelines and routines
- Regulations for users of ICT resources
- Guidelines for implementing access to emails and files [In Norwegian]
- Guidelines for disclosure of digital material to the police [In Norwegian]
- Guidelines on the prohibition of the use of certain digital services [In Norwegian]
- Guidelines for handing over and handing in ICT equipment for UiT's employees [In Norwegian]
Chapter 12: International cooperation and export control
This chapter has been approved, however for the time being it's only available in Norwegian. It will be translated to English, and then posted here.
Chapter 13: Internal control and auditing
This chapter has been updated. The Norwegian language version is the updated version. The English version will be updated, but until then only the Norwegian language version is valid.
The purpose of control activities is to be able to assess the extent to which the established measures are sufficient and effective in order to ensure compliance with relevant regulations and general guidelines. Through controlling activities, areas of improvement related to existing measures may be identified and identified any further measures that should be implemented.
UiT's control activities within information security and privacy will consist of both regular activities that are carried out regularly, as well as activities that are carried out if necessary. Examples of regular activities are the annual status report all units provide with mapping of information values as well as self-assessment of the state of the unit.
The more detailed control activities are regulated by guidelines for UiT's control activities within information security and privacy, which are determined by the IT Director. This guideline shall contain both an overview of the fixed control activities, as well as regulation of the type of activity carried out if necessary, including who can decide implementation. Furthermore, requirements for documentation related to the various activities will also be regulated by the guideline and any associated routines.
Internal Audit
Internal audit of the information security and privacy management system shall be carried out if necessary, and as a general rule at least every five years.
Chapter 14: Handling incidents and nonconformities
This chapter has been updated. The Norwegian language version is the updated version. The English version will be updated, but until then only the Norwegian language version is valid.
Nonconformities are violations of laws, regulations, or internal regulations at UiT. Reported nonconformities and their handling are a key source for both assessing the safety level at the units where nonconformities occur as well as for UiT as a whole, and through this uncovering the need for new or adjustments to existing security measures. Thus, nonconformity management is about quality and improvement, in addition to damage limitation.
In this context, nonconformities and incidents may be of a security nature, and/or a breach of data protection legislation.
Examples of events and nonconformities:
- theft of computer equipment
- misuse of IT services
- password misuse
- invoice fraud
- computer attacks
- data leak
- ransomware
- weaknesses in IT systems
- violation of, or lack of, routines at UiT
- confidential information astray
- unauthorized access to information
- use of data processor without sufficient agreement
- collection of personal data beyond what was legitimately needed (violation of the data minimization principle)
- processing of personal data without a lawful basis, including further processing for new purposes without having valid, legal grounds to this
Notification and handling of incidents and nonconformities
The person who discovers, or is made aware of, incidents and deviations (hereinafter "incidents") shall report this to the Privacy and information security office ("FPI") as soon as possible. Practical procedures for reporting incidents is determined by FPI and is described at uit.no/security.
FPI investigates the causes of the incident and the need for corrective measures. The responsibility for planning and implementing corrective measures will normally lie with the unit where the incident occurred, but it lies with FPI to decide how the incident should be handled. FPI has the authority to involve the personnel resources necessary to follow up and close an incident.
FPI shall keep an overall overview of all incidents that have been reported. These will be included in the annual management's review and will be used for learning across the organization to prevent recurrence.
In the event of major incidents and/or incidents where it is appropriate to report the incident to the Norwegian Data Protection Authority, FPI will routinely inform the management of the relevant unit on the matter.
Notification to the Norwegian Data Protection Authority
In the event of incidents involving breaches of personal data security, UiT as data controller shall notify the Norwegian Data Protection Authority without undue delay and, where possible, no later than 72 hours after learning of the incident, unless it is unlikely that the breach will entail a risk to the rights and freedoms of natural persons. It is therefore very important that incidnts are reported via UiTs incident-system as quickly as possible.
Notification to the Norwegian Data Protection Authority shall go via the Privacy and information security office ("FPI"); the units shall not submit such a message themselves.
If FPI considers that the duty to notify has occurred, they have the authority to send the notification to the Norwegian Data Protection Authority on behalf of UiT. The IT director decides whether all or part of FPI shall have such authority. Information on such matters must always be forwarded to the top management of UiT, via the director of administration. If the nature of the case dictates, the director of administration shall be actively involved in the handling of the matter, including the preparation of the report, from as early a time as possible.
The Data Protection Officer shall always be informed of reports to the Norwegian Data Protection Authority. As far as possible, the Data Protection Officer shall be informed of the matter and access the report before it is sent. If the nature of the case dictates, the data protection officer shall be directly involved in the handling of the incident from as early a time as possible. However, the Data Protection Officer always has the opportunity to actively engage in the handling of all incidents involving breaches, or potential breaches, of personal data security. FPI shall confer with the Data Protection Officer before a decision is made if the assessment indicates that the duty to notify does not occur.
Chapter 15: The management's review
This chapter has been updated. The Norwegian language version is the updated version. The English version will be updated, but until then only the Norwegian language version is valid.
In aid to management, a report shall be prepared annually that reviews the work on information security and privacy. This is included in the annual report on information security and privacy at UiT, and is promoted to the University Board during the first quarter of the following year. The report is prepared by the Privacy and information security office. The Data Protection Officer prepares its own annual report that is submitted to the University Board in a separate case. As far as possible, the Data Protection Officer's annual report will be presented to the Board at the same meeting as the annual report on information security and privacy.
Management's review shall include
- nonconformities and incidents, including any trends that should be paid special attention to
- the risk picture for UiT
- results/follow-up of control activities
- results/follow-up of internal audit, if applicable
- the condition of risk management at UiT
- status of adopted measures from the previous review
- need for adjustments to the management system
- resource and competence needs, including whether there is a special need for the coming year
In addition to this regular, annual reporting, meetings shall be held with management if necessary; for example, if the balance of risk changes, control activities or incidents reveal issues and situations in which management must be actively involved, and the like.
Follow-up of the annual report in the individual units at UiT
In addition to the senior management at UiT, the management at the individual units has a considerable responsibility in safeguarding information security and privacy.
Units with their own board
After the report has been considered by the University Board, it must be presented to the boards of the individual units at UiT. In addition to the annual report, the case for the unit boards must also address specific issues and areas of improvement for their own unit. It is the management of the unit in question that is responsible for the preparation and presentation of the case to the board of directors in question. The Privacy and information security office shall have access to the board case.
Administrative departments under UiT’s top management
After the report has been considered by the University Board, it shall be sent to all departments of the joint administration ("Level 1"). The report shall be addressed in their internal management meetings, where special issues and the area of improvement for their own unit also shall be addressed. The director of the department is responsible for the preparation and presentation of the matter for the management meeting, and the review must be documented. The Privacy and information security office shall have access to this documentation.
If possible, the Data Protection Officer's annual report will also be presented to the unit boards and administrative departments and if so shall be handled the same way as the annual report on information security and privacy.
We are working on e-learning modules on information security and data protection. In conjunction with the National Cyber Security Awareness Month, UiT created its own courses on information security. You are encouraged to complete these! Go to https://go.nanolearning.com/LessonViewer/?d=468736&key=2FvQUpIbbtJsl7FF&intranetpage=true
It is important that all units have detailed procedures for the handling of information security at their unit, e.g. handling of print outs of confidential information, procedures for conducting and approving risk assessments, etc. – adapted for your unit.
We will publish some guidance and information about what you need to be aware of on this page.
Office 365
For research data, we recommend using SharePoint. OneDrive is personal storage that will be deleted automatically if the user leaves the institution.
Confidential information and personal data may only be stored on Windows computers administered by UiT. Privately owned equipment (laptops/computers, mobile devices), Mac or Linux are currently not approved. For further information about what type of data the various services in Office 365 are approved for, please see above (“Which services can you use for different types of information/data?”)
For practical information about how to classify your data and secure data processing in Office 365, please refer to IT support/Orakelet’s user instructions
Training modules
Here you will find basic training modules for information security and data protection/privacy.
The lessons are set in the recommended order.
First is part 1 which is the basic training, and in part 2 there are some modules about everyday security, i.e. practical tips, info etc.
Please note: All the links will be published in short order, in the mean time you can reach the modules through https://uit.no/sikkerhet/kurs (the links from the norwegian version of this page will work, as you get a choice between norwegian or english when you start the training modules themselves).

| Information security |  |
| Module | Info |
| What is information security? |
This training lesson gives an overview of what information security is, and a little about why it is important for everyone who works or studies at UiT. |
| Why is information security important? |
In this lesson, you'll learn a little more about why good information security is important. |
| The threat picture - an overview |
In this training session, you will get an insight into the threat and risk picture at UiT, which will contribute to a better understanding of the challenges we face. |
| The threat picture - especially about state actors | This training lesson provides an overview of threats to information security at universities, with a particular focus on risks from state actors and how these can affect research, collaboration and values at UiT. |
| How to ensure information security |
|
| Measures to reduce risk | In this lesson, you'll learn more about how you can help reduce risk |
| Approved services and systems at UiT | In this lesson, you will get more information about approved services and systems at UiT and why they should be used. |
| Knowledge test - information security | Here you can take a small test of what you have just learned |
| Privacy / data protection |  |
| Module | Info |
| What is privacy? | In this lesson, you'll learn a little about what privacy is, and why it's about more than just information security |
| Why is privacy important? | In the previous lesson, you learned a little about what privacy is, and in this one, we will briefly review why it is important. |
| Key concepts and roles in privacy | This training lesson gives you a simple introduction to the key concepts and roles of privacy and GDPR. |
| Knowledge test - basic course in privacy | Here you can take a small test of what you have just learned |
| Classification of information |  |
| Module | Info |
| About information values | In this lesson, you'll learn more about different types of information values |
| Why classify the information? | In this lesson, you will get more information about why all information at UiT should be classified |
| How to classify | In the previous lessons, you learned about informational values and why they need to be classified. You will now learn how we divide information into different levels of protection ("classify") so that we can take good care of our information and make sure it is accurate and available when we need it. |
| Knowledge test - classification of information | Here you can take a small test of what you have just learned |
| Risk assessment |  |
| Module | Info |
| What is a risk assessment? | In this lesson, you'll learn more about what a risk assessment is and what it contributes to |
| Non-conformities/incidents |  |
| Modules | Info |
| What are non-conformities, and how to report them? | This lesson gives you a simple introduction to what counts as non-conformities in information security and privacy, and how you can easily report such incidents. |
| Overview |  |
| Module | Info |
| The Security, Emergency Preparedness and Data Protection Management system | In this lesson, we will provide some information about what UiT's management system for security, preparedness and privacy is, and why we have it. |
Have a secure digital workday
Just about whatever your job is, you will use several digital tools during your work day. It is important to know how to keep yourself and the data you work with secure, be it that you work from your office or your home. Here we will present some information to help you achieve better security, and get to know some of the important rules and regulations governing information security and data protection at UiT.
Working from home
After corona it's more common that UiT’s employees are working from home part of the time. However, it is important that data protection and information security are still safeguarded, and you have an important responsibility in this respect.
UiT manages vast amounts of research data, as well as personal data about employees, students, research participants, guests, partners and others, and other information of great importance to the organisation. Failure here can cause significant harm to UiT and individuals. Attending to information security and data protection is your responsibility and is fulfilled by being careful, complying with relevant legislation, guidelines and procedures, and reporting any undesirable incidents you discover or experience.
If there are other people in your household, remember that your duty of confidentiality also applies to them. This can easily be overlooked if you leave papers lying around, your computer is unlocked or you lend it to your children or you conduct Skype meetings with others present in the room, etc.
Consequently, we would like you remind you of some rules that everyone must be aware of (whenever you are working from home, including post-Corona):
Basic rules
- Work involving confidential (red) and strictly confidential (black) data shall only occur on equipment owned by UiT.
- Papers and notes must be stored in such a way that others in your household cannot read them.
- ICT equipment owned by UIT (e.g. computers and tablets) must not be loaned to others in your household, including children.
- This is not only because they can gain access to confidential information, but they can also erase or share the information by mistake.
- Moreover, we wish to minimise the risk of your device getting malware (which can steel or destroy information, e.g. a crypto virus), and one of the measures to achieve this is that only you use the device and only in a work-related context.
- Private cloud computing services (e.g. Dropbox) shall not be used
- You must lock your screen when you leave the computer unattended (even for short periods) if other people are home.
- Learn to use the keyboard shortcut Win + L to lock your screen quickly:
- On UiT’s computers, you can activate a PIN code to avoid entering your password every time you need to unlock the screen. With newer computers face recognition can also be utilised.
Skype/video meetings
Communication tools like Skype, Teams and Adobe Connect, etc. will be widely used for meetings, teaching, etc. As confidential topics are often discussed (especially during meetings), it is important to be aware of your surroundings. This also applies to teaching, e.g. when you are holding seminars and tutorials. Students expect to ask questions and share their views with you, not you and your immediate family.Please be aware of the following:
- If others are present in the room, you must use a headset
- We recommend this anyway as using a headset enhances sound quality and reduces background noise.
- Be conscious of what you are say if others are present in the room.
- We remind you about the duty of confidentiality.
VPN
Unless you need to reach services that require you to be connected to UiT’s network (e.g. Ephorte, PAGA, the home drive, etc.), you do not have to be connected to VPN.The communication with Office 365 (e-mail, OneDrive, SharePoint, Teams, etc.) is encrypted and thus VPN is unnecessary.
- Owing to the large number of people who are now working outside the campus, we ask that you are not connected to VPN if this is unnecessary.
- VPN may be required for certain updates on your computer. We will publish a message here and as an operational message if you need to do something and, if so, how.
- This does not apply to all updates, e.g. Microsoft (Windows/Office) updates will function normally.
How to avoid attempted scams and attacks
There is an ever present challenge with criminals and other hostile actors trying to scam or otherwise attack UiT. They will continuously come up with new methods, and will try to exploit periods of big changes or vulnerabilites.
For instance, during the Corona pandemic Norway and other parts of the world quickly experiened that criminalst tried to exploit the upheaval caused by the pandemic. There is a vast requirement for information, employees are working at different locations than usual (such as at home) and following different routines and there is rapid development and exchange of information about how to do this. Dishonest and criminal actors are trying to exploit this by hacking into IT systems, steal personal data and committing financial crime, etc.
Consequently, it is especially important to be careful during this period because we know that UiT can be exposed to purposeful attacks. It does not have to be an “IT attacks” where someone tries to hack into systems, but may be “social manipulation” where someone impersonates a person, company or organisation to create trust and entice you into divulging or changing information or accesses. They may also try to get you to install malicious programs (“malware”), which give them direct access to your computer and perhaps the systems, storage services, etc. you have access to at UiT.
Consequently, we will remind you of some of the things you need to be especially aware of. These tips are basically no different from those that apply at other times. However, as mentioned, we can expect additional activity during this period. As such, many of the examples deal directly with the Corona virus (COVID 19).
- We can expect phishing attacks to increase in volume.
- Do you want to read more about phishing and how to discover it? See this lesson (https://app.xtramile.no/new/training/d2caa932-96ca-4566-8aa3- 3a3567ec81fb) UiT created in conjunction with National Cyber Security Awareness Month.
- Be extra vigilant if you receive e-mail related to the Corona virus.
- Naturally, you will receive some legitimate e-mail related to the Corona virus, but check the content, context and sender carefully. For information about how to check if an e-mail is legitimate, please send the link in the point above.
- This involves knowledge and habits that are useful at other times too, both in a work and private context.
- False/illegitimate e-mail will often try to
- play on fear
- deal with financial interests (such as “updated delivery info”, “amended payment details”, etc.)
- get the recipient to act in haste (“Important!”, “Respond immediately”, “Urgent clarification required” etc.)
- give the impression they are a public body/authority (such as WHO, FHI, etc.) or employer and encourage you to implement immediate action
- UiT will provide messages about measures via en.uit.no/corona. We may send updates by e-mail, but the information in these will be reflected on https://en.uit.no/corona or in the official operational messages. If you don’t find it there and the e-mail asks you to log in to a website, open an attachment or install a program, take the time to check the content before you do anything further.
- If you are in doubt, ask your manager or a colleague if this is genuine.
- WHO does not send out e-mail that require you to log in to gain access to the information, attachments that you have not requested or information on pages outside the domain www.who.int.
- get you to click on/open evil-minded links or attachments
- If you are not expecting an e-mail, check that it is genuine, see the point above about phishing attacks.
Still in doubt? send a question about the e-mail to sikkerhet@UiT.no (mailto:sikkerhet@UiT.no)
More information:
SMS
There have been cases in Norway where employees have received an SMS that gives the impression that it is from the management. They were asked to install a specific tool to simplify the communication while they are working from home. That was an attempted scam and the “tool” in question was malware.
- UiT would not provide this type of information via SMS.
More information about "smishing"
Example from Norway
Phone
You may also receive phone calls from scammers.
- For example, “Microsoft” will be extra active at this time. Scammers claiming to be from Microsoft (sometimes they say they are calling from Windows) will call and say they have discovered a problem with your computer that they can help you with. Microsoft would not call anyone like this, so just hang up if you receive such calls.
- The phone number they call from can be a Norwegian number, an overseas number or neither (just a collection of numbers). This is because they hide their real number and give the impression that they are someone else. The actual owner of the phone number has nothing to do with call and have not been hacked (the scammers have simply chosen a number, which they give the impression is their own number).
- If you have followed the scammer’s instructions, in full or in part, please notify sikkerhet@uit.no immediately so we can help you.
Websites
Many false websites have been created to take advantage of the situation the society is now in
- This includes a false “coronavirus map” that claims to be providing “live” information about the spread of the virus. It is actually malware.
- These sites are usually based on the information and appearance of genuine sites and can be challenging to uncover.
- “Fake news” is a recurring problem, including in this situation. Be vigilant and practice source criticism.
Examples:
- https://nrkbeta.no/2020/03/11/slik-spres-falske-nyheter-om-koronaviruset/
- https://www.forbes.com/sites/thomasbrewster/2020/03/12/coronavirus-scam-alert-watch-out-for-these-risky-covid-19-websites-and-emails/#880fff71099f
- https://www.digi.no/artikler/slik-bruker-hackere-koronavirus-frykten-til-a-spre-skadevare/487347
More information/sources
Here are some links to more information. Please be aware that the advice to employees/users here is general. In a work-related context, please follow the advice given by UiT.Does something look not quite right? Please contact sikkerhet@uit.no and we can have a chat about it.
- https://www.nsr-org.no/aktuelt/svindelforsok-og-angrep-relatert-til-covid-19 [in Norwegian]
- https://nsm.no/fagomrader/digital-sikkerhet/nasjonalt-cybersikkerhetssenter/varsler-fra-ncsc/varsel-i-forbindelse-med-koronaviruset [in Norwegian]
- https://www.nrk.no/osloogviken/fikk-sms-fra-_sjefen_-_-viste-seg-a-vaere-korona-svindel-1.14942801 [in Norwegian]
- https://www.digi.no/artikler/slik-bruker-hackere-koronavirus-frykten-til-a-spre-skadevare/487347 [in Norwegian]
- https://nrkbeta.no/2020/03/11/slik-spres-falske-nyheter-om-koronaviruset/ [in Norwegian]
- https://www.forbes.com/sites/thomasbrewster/2020/03/12/coronavirus-scam-alert-watch-out-for-these-risky-covid-19-websites-and-emails/#880fff71099f
See "About risk assessments"
About risk assessments
- when the threat level changes
- prior to starting the processing of personal data
- at the start of research projects
- when establishing or changing ICT systems
- when organisational changes are made that may affect the information security
Acceptable risk
It is not possible to eliminate every risk, but UiT will work systematically and purposefully to have a risk level that is acceptable, seen in relation to UiT's goals and risk picture.
UiT shall have a risk-based approach to information security, and "acceptable risk" is thelevel of risk UiT is willing to accept in order to create value and achieve the goals and benefits sought.
Risk appetite can be categorized in different ways:
- Unwilling: Should avoid risk.
- Minimalist: Extremely conservative.
- Caution: Should avoid unnecessary risk.
- Flexible: Will take strongly justified risks.
- Open: Will take justified risks.
Too high a risk appetite on UiT's part will expose employees, students and research participants to an unsustainable risk of harm and negative consequences, as well as could damage UiT's reputation and / or have financial consequences. Too low risk appetite will mean that projects, processes, activities, etc. are not feasible either because it is not possible to bring the risk down to a very low level, or it will be disproportionately time-consuming and expensive. This could have major negative effects on UiT's activities.
The stronger and better the security culture, basic security, and systematics around the work with information security throughout the university, the greater the scope for implementing ambitious projects and processes which in an organization with a weaker security culture and work will entail an unacceptable risk. Both UiT's risk picture and overall basis for managing risk in a responsible and trustworthy manner will be dynamic, and must be continuously assessed, including measuring the safety culture among employees and students.
As a rule, therefore, "acceptable risk" will be in the middle three categories ("minimalist", "cautious" and "flexible"). This may vary based on, for example, the type of data processed, the benefits sought to be achieved and the risk involved in not initiating a process, carrying out a research project, adopting an IT system, etc. However, it is not up to the individual's discretion how risk is to be assessed, or what level of risk can be accepted. Therefore an account of how UiT assesses risk, as well as the limits for acceptable risk, is set.
Risk levels
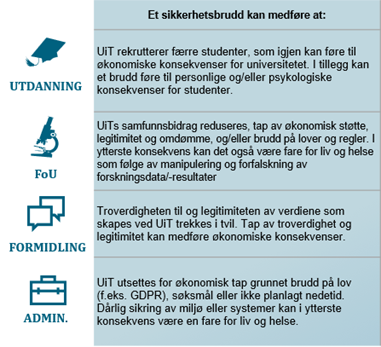
Undesirable incidents can lead to breaches of information security, which means breaches of the information
- Confidentiality: the information shall not be known to unauthorized persons
- Integrity: the information shall not be altered unintentionally or by unauthorized persons
- Availability: the information is available when legitimately needed
Breaches of information security can have consequences for all parts of UiT's activities, for example [the example is only available in Norwegian for now]:
The risk level is the sum of the probability of an undesired event occurring, and the consequence if it occurs. This is mapped and assessed through risk assessments (see chapter 5 of the management system).
The probability of an undesired event occurring is assessed on a scale from 1 – 4, according to a set of criteria established by UiT.
The consequences if an undesired event should occur are assessed on a scale from 1 – 4, according to a set of criteria established by UiT.
The risk level for the adverse events is categorized into four levels:
- 7 – 8 Very high risk
- 6 High risk
- 4 – 5 Moderate risk
- 2 – 3 Low risk
To ensure that there is as similar and correct an assessment as possible of which risk UiT is willing to accept, it is necessary to set some general requirements for the management of identified risks, see below under "requirements for the management of identified risks (undesirable incidents").
Moreover, it is necessary to set some more absolute outer limits that should not be passed, no matter what gain can be obtained. The latter is determined by the University Board, see below under "the outer limit of acceptable risk".
The type of data, and the associated classification according to UiT's guidelines for classification of information (chapter 3 of the management system), will be a key part of the basis for the assessment.
Requirement for handling identified risks/non-conformities
| 7-8 |
Risk-reducing measures shall be implemented. If the risk cannot be reduced from the red level through measures, the following applies:
If the risk relates to possible breaches of confidentiality for strictly confidential/black data, then it's not possible to
|
| 6 |
If the risk cannot be reduced from the orange level through measures:
|
| 4-5 |
|
| 2-3 | Risk-reducing measures may be considered. |
*By unit manager is meant dean, director UMAK, director UB, department director. The rector and the chief administrative officer can also make these decisions.
- Security-related irregularities (e.g. passwords that have gone astray) that require rapid measures of a technical nature are reported to CSIRT.
- Other information security-related nonconformities shall be reported to sikkerhet@uit.no.
- What has happened, where did it happen and how did it occur?
- The date and time span of the breach/nonconformity
- When it was discovered
- Have unauthorised persons become aware of (or potentially become aware of) information?
- If so, can you say something about this, e.g. the number of people, describe the situation (published on the internet, sent by mistake to one person, etc.)
- Has the information been lost or unavailable for some time (did this create major or minor consequences)?
- Has the information been changed (either by unauthorised persons or by accident)?
- How many people are affected by the breach/nonconformity (approximately if you don’t have an exact answer)?
- Who we can contact to get more information, if necessary?
UiT uses various services and it is important that these services are used for the purpose they are intended. In addition to ensuring that data is kept sufficiently “secret”, we must safeguard the availability (What happens if your data are lost and they were stored in a service without adequate backup? Or an examination is held digitally, and the service stops midway through the examination?) and the integrity (What happens if someone can change your research data without you knowing about it? Or their examination grade?) in an adequate manner.
Furthermore, we are subject to various laws that impose requirements about the quality and terms of the services we utilise, not least GDPR. We will publish information here about what the services are approved for (initially related to confidentiality requirements), as well as information about the degree to which you can use services other than those purchased by UiT.
Other collaboration tools than those provided by UiT. Can you use them?
Other digital collaboration tools
- The use of digital collaboration tools other than those offered by UiT via the Department of Information Technology is not permitted. There might be some exeptions if the necessary agreements are in place, but this is not something that every employee can enter into themselves. Please check with the IT Department first, if you are wondering if a given tool is permitted to use.
- We are subject to various statutory provisions and, among other things, data processor agreements must be entered into (which are reviewed for quality assurance (see the checklist for Data processor agreements) and risk assessment, cf. The Information Security Management System Chapter 1, cf. Chapter 5 (https://UiT.no/sikkerhet(/sikkerhet)).
- Major differences will often exist between the agreements UiT enters into, e.g. through sectorial cooperation, and those entered into by departments, which are often direct with contractors. This may be reflected in the terms for processing of data or where data is stored (USA instead of EU/EEA), etc.
- If the existing digital collaboration tools do not meet the unit is requirements, please contact the Section for Digital Platform and Operation (VITE) the Department of Information Technology.
- Please note: This does not apply to external meetings you have been notified of. If you plan to participate in a meeting with, for instance, UiO and you have received a link to a (virtual) meeting room using a tool that UiO utilises, of course you may participate.
Private licences
The use of private licences in a work context is not permitted; primarily because it involves processing UiT data (including about students and colleagues) in private context, but also with respect to what the license itself permits. Moreover, by definition, UiT loses control over the data and cannot fulfil its statutory requirements pursuant to GDPR, etc.
Licences via other Higher Education institutions
- Do you have an employment relationship with another institution that has a service you wish to use in a teaching context, i.e. implement teaching activities that are under UiT under the auspices of UiT and involve UiT’s students?
- This will require agreements between UiT and the relevant institution, e.g. a data processor agreement if it involves personal data, because the other institution would actually be processing data on UiT’s behalf. Furthermore, a risk assessment must be conducted to ensure that the data can be handled adequately in the relevant service.
- Therefore, you must only use the services you have access to via UiT directly.
Which services can you use for which content?
UiT has numerous systems and services that can and must be used. However, not all these are approved for all types of data. Based on the management system, all information at UiT is classified as either open (green), internal use (yellow), confidential (red) or strictly confidential (black). The types of data the various services and systems are approved for, and what is needed for this approval to apply, is determined through the risk assessments.
The table below shows an overview of which data can be processed where.
You will see that some systems/services have footnotes, which relate to the list below the table. These include key conditions for the approval to apply. However, using the service or system as specified in the guidelines, training etc. will always be one such condition. It is important to follow the guidelines, procedures, etc. because UiT uses such documents to implement measures are required for a given type of information to be processed in the system or service.
If you use the system or service in a manner other than described/stipulated, the information in the table does not apply and you must contact the system owner directly to clarify whether the use is allowed.
Are you wondering what the different categories mean? See the guidelines in Chapter 3 of the management system.
| System/service | Open/Green | Internal/Yellow | Confidential/Red | Stricktly confidential/Black | Data Processor |
| Canvas | OK | OK | Not approved | Not approved | Instructure |
| CENT | OK | OK | OK | Not approved | |
| Chat.uit.no | OK | OK | OK | Not approved | Not applicable |
| CLARC | OK | OK | OK | Not approved | |
| DataverseNO | OK | Not approved | Not approved | Not approved | Microsoft and UiO |
| Elements | OK | OK | OK | OK | Sikri |
| E-mail (Office 365) | OK | OK | Not approved | Not approved | Microsoft |
| EUTRO | OK | OK | OK | OK | UiO |
| Shared areas (F:\) | OK | OK | Not approved | Not approved | Not applicable |
| Felles studentsystem (FS) | OK | OK | Not approved | Not approved | Sikt |
| Forms (Office 365) | OK | OK | Not approved | Not approved | Microsoft |
| Hunt Cloud6 | OK | OK | OK | OK | |
| Jatos | OK | OK | Not approved | Not approved | Microsoft |
| Klartekst.uit.no | OK | OK | OK | Not approved | Not applicable |
| LOIS | OK | OK | Not approved | Not approved | |
| Nettskjema / Secure Nettskjema | OK | OK | OK1 | Not approved | UiO |
| NIRD | OK | OK | Not approved | Not approved | |
| NIRD Archive | OK | OK | Not approved | Not approved | |
| NREC | Ok | OK | Not approved | Not approved | |
| NSD | OK | OK | OK | Not approved | |
| OneDrive for Business (Office 365) | OK | OK | OK2 | Not approved | Microsoft |
| Panopto | OK | OK | Not approved | Not approved | Panopto |
| Planner | OK | OK | Not approved | Not approved | Microsoft |
| REDCap | OK | OK | OK | Not approved | Microsoft |
| RSpace | OK | OK | Not approved | Not approved | Research Innovations Ltd |
| Sharepoint (Office 365) | OK | OK | OK2 | Not approved | Microsoft |
| Stream (Office 365) | OK | OK | Not approved | Not approved | Microsoft |
| Sway (Office 365) | OK | Not approved | Not approved | Not approved | Microsoft |
| Teams (Office 365) - files | OK | OK | OK2 | Not approved | Microsoft |
| Teams (Office 365) - meetings | OK | OK | OK3 | Not approved | Microsoft |
| TopDesk | OK | OK | OK5 | Not approved | TOPDesk |
| Tjeneste for sensitive data (TSD) | OK | OK | OK | OK | UiO |
| Viva Engage (Office 365) | OK | Not approved | Not approved | Not approved | |
| WiseFlow | OK | OK | OK4 | Not approved | UNIwise |
1 = The service “sikkert nettskjema” (secure online form) must be used for confidential information. Contact the Section for Digital Research Services (SDF) (/om/enhet/forsiden? p_dimension_id=88223). “Nettskjema (/om/enhet/Article?p_document_id=513952&p_dimension_id=88225)” (online form) is only for open and internal information.
2 = This is conditional on the following security measures being followed: classification of information, two-step verification is activated. Information that is subject to restrictions of processing in Norway (e.g. pursuant to the provisions of the Security Act) cannot be processed here either.
Please note: The chat function in Teams is not encrypted.
3 = For Teams meetings with confidential content, it's recommended to enable the "lobbying feature" so that the host must actively let in the people who are trying to connect to the meeting. Participants must use a camera. Ask for ID if there are any meeting participants you don't know. Do not record the meeting. Do not use the instant messaging (chat) feature for red data
4 = Sensitive personal data (e.g. medical certificates) shall not be processed in WiseFlow. However, confidential information, such as examination question papers before the examination is held, can be processed in this service.
5 = If TopDesk shall be used for confidential data, prior approval is required (before the operator queue is established).
6 = As of now the agreement with Hunt Cloud is only valid for part of the Faculty of Health Sciences
Use of video
If you would like information and guidance about how to use video in teaching, please check https://UiT.no/digitalundervisning (/digitalundervisning).
This page features resources and guidelines associated with when you can use video, what you need to monitor, which assessments are required, etc. This relates not only in a teaching context, but also in other activities at UiT.
If there are people involved in the video, this will generally involve personal data. Consequently, GDPR must be followed, which involves the following requirements:
- A basis of processing is required, i.e. a lawful basis (in GDPR) for processing personal data.
- Those who are in the video (either directly or indirectly) must be informed about this. This applies irrespective of whether the video is only streamed or also recorded.
- Information security must be attended to and you must consider how long the video shall be available. When the purpose of the recording no longer exists (e.g. after the semester /re-sit examination has ended), it must be deleted (not just deactivated).
You can read more about this and other topics in the submenus below.
All processing of personal data must have a basis for the processing pursuant to GDPR. This is an absolute and unavoidable requirement. The controller (the person who makes key decisions associated with the processing, such as the purpose and which means shall be utilised) must have this basis in place. This guidance assumes that UiT is the controller. In instances where UiT acts as a “data processor”, the contractor must have the basis for the processing in place, while UiT must ensure that we have an adequate data processor agreement before we receive the personal data.
Legal basis for processing personal data
During the period when lectures and seminars at UiT’s campuses/physical locations are cancelled, digital lectures and seminars will be utilised where possible.
A legal basis for the processing is always required.
UiT has categorised various activities where video is utilised (in teaching, examinations, dissemination and for administrative purposes). These activities have so many similarities that we have decided a relevant basis for the processing – for the personal data of both the employees and the students.
Important: It is essential that the unit/lecturer always assesses whether, for instance, video is necessary and, if it is deemed necessary, whether streaming the video is sufficient or if it must be recorded? Is it possible to combine different teaching methods, e.g. publishing a video from a lecturer followed by a chat discussion? These are just examples, and this is largely an academic (educational) decision. However, it is necessary to consider this. One must always undertake such a necessity consideration for the processing of personal data to be lawful. In other words, one cannot simply point to a given basis for the processing and then take it as a “blank authorization”. There must be a balance between what is achieved and how comprehensive this is for the student and the employee, and whether one can utilise means to reduce this impact on employees and students.
General/introduction
Many people often think of GDPR as a “consent law”, i.e. if you are going to process personal data, you must have consent from the person(s) the data applies to. However, this is incorrect. There are numerous bases for the processing and consent is just one of these. For teaching and administrative purposes, consent will often not be applicable and other bases must be used.
Basis for the processing is referred to in two different articles in GDPR:
- For general personal data (most types of data): Article 6
- For special categories of personal data (health, religion, politics, etc.): Article 9 (in addition to Art. 6)
Furthermore, several of the bases for the processing in GDPR require a so-called supplemental authority (“where Union or Member State law”).
- 6 (1) (c): the processing is necessary for compliance with a legal obligation to which the controller is subject
- If this basis for the processing is used, one must refer to a correct legal obligation to which UiT is subject (via an act or regulation)
- 6 (1) (e) the processing is necessary for the performance of a task carried out in the public interest or in the exercise of official authority vested in the controller
- If this basis for the processing is used, one must be able to show that a “task in the public interest” or “exercise of official authority” is vested in UiT. One must also refer to the correct provisions in this context.
- This also applies to several of the bases pursuant to Article 9.
Specifically about consent
Consent is probably the “best known” basis for the processing. We find this basis in both Article 6 (1) (a) and Article 9 (2) (a). However, it is a widespread misunderstanding that consent is the only basis for the processing (“If you are going to process personal data, you must have consent”) or that consent is the preferred basis for the processing and that the order in Articles 6 and 9 give the impression of a “ranking”. This is incorrect. Consent is one of several possible bases for the processing, and these have equal status. Moreover, there is not necessarily any conflict between using any of the other bases for the processing and the fact that the subjects participate freely.
There will be some instances where it will be correct to use consent and where perhaps it will be the only relevant basis for the processing (e.g. this is often the case in research projects).
If one plans to use consent, one must be certain that this consent is valid pursuant to GDPR, as numerous conditions must be met for the consent to be valid. If even one of these conditions are not met, then the consent will be invalid. The consequence will be that the processing is unlawful and nay data collected or generated on the basis of the consent in question must be erased. Reactions can also come from regulatory authorities. In these situations, it will not “help” if you have obtained a consent from everyone because, if the validity conditions are not met, the processing is unlawful.
For UiT, there are numerous situations where we are prevented from using consent as a basis for the processing, and it is important to be aware of this. We will now look briefly at the conditions for consent, especially one that is often problematic for UiT to meet. The conditions for consent are stipulated in Article 4 (11) cf. Art. 7 of GDPR.
However, it is important to emphasize that there are certain limits about what one can consent to. A consent pursuant to GDPR is only a basis of the processing. This means that a person cannot, for instance, consent to other requirements in GDPR being deviated from (e.g. the requirement concerning information security).
Consent must be freely given, specific, informed and unambiguous. If it applies to personal data, the data subject must give his/her consent by a statement or clear affirmative action. Furthermore, it must be possible to demonstrate that the data subject has consented to processing of his or her personal data. If the consent is given in the context of a written declaration that also concerns other matters, the request for consent shall be presented in a manner that is clearly distinguishable from the other matters in the declaration. It must be given in an intelligible and easily accessible form, using clear and plain language. If the processing activities can be distinguished from one another, one must ensure that the consent is not obtained in an ‘’everything or nothing’’ form. The person must have a choice between the various processing activities. A consent may be withdrawn at any time, and the data subject shall be informed of this prior to giving his or her consent. The processing of the personal data about this person must then cease, which often involves erasing the data. Moreover, it shall be as easy to withdraw as to give consent, i.e. If consent can be given with “one click”, it must be possible to withdraw it with “one click”. Finally, it is important to be aware that passive consent is invalid. An active action is required (e.g. ticking a check box. If the box is pre ticked, it means the consent is invalid).
Consequently, many requirements must be fulfilled for a consent to be valid. One must keep track of who has given their consent and be ready to act if someone withdraws their consent.
However, for UiT, we must pay particular attention to the condition that consent must be given freely.
The consent shall genuinely be freely given. When there exists an imbalance of power between the controller and the relevant data subject, this is extremely difficult to achieve. This is described in the following manner in point 43 of the preamble in GDPR (our emphasis): “In order to ensure that consent is freely given, consent should not provide a valid legal ground for the processing of personal data in a specific case where there is a clear imbalance between the data subject and the controller (...)”.
In working conditions, it will be difficult to meet the requirement that consent be given freely, owing to the uneven balance of power between employer and employee. It is not entirely inconceivable but, in the vast majority of cases, one should avoid trying to use consent as the basis for the processing. Please note that this does not mean it never can be voluntary for an employee to, for instance, perform a task or give information. However, the everyday understanding of “freely given” has a much lower threshold than GDPR. WP29 (advisory group in the EU) stated the following about this question [1] (our emphasis):
“There may be situations when it is possible for the employer to demonstrate that consent actually is freely given. Given the imbalance of power between an employer and its staff members, employees can only give free consent in exceptional circumstances, when it will have no adverse consequences at all whether or not they give consent. [Example 5:] A film crew is going to be filming in a certain part of an office. The employer asks all the employees who sit in that area for their consent to be filmed, as they may appear in the background of the video. Those who do not want to be filmed are not penalize in any way but instead are given equivalent desks elsewhere in the building for the duration of the filming”.
There does not need to be explicit ‘threats’ of reactions if one does not consent, or more obvious pressure, for the requirement relating to ‘freely given’ not to be met. More implicit or informal pressure or expectations (“this is desirable for UiT to achieve”, “everyone must pull together”, etc.) will also lead to the requirement relating to ‘freely given’ not being met. Consequently, as an employer, UiT should not use consent as a basis for the processing. However, if one still chooses to use this, it must be thoroughly reasoned and discussed, particularly concerning the requirement relating to ‘freely given’.
Many of the above-mentioned considerations are also applicable when it comes to processing of the students’ personal data. This is a clear imbalance of power between UiT and the students. This applies to everything from UiT as the overall institution to the lecturers. Consequently, UiT must be extremely constrained in the use of consent as a basis for the processing of the students’ personal data, especially in a teaching context. This does not mean that there are not instances when the use of consent is both relevant and correct. However, in such cases, one must ensure that through and documented assessments have been implemented. The main rule is that other bases for the processing should be utilised.
Specifically regarding the situation with Corona (for the time periods when national measures are in place):
Given the situation UiT is currently in with Corona-related measures and the fact that all instruction must be digital for an unknown period, it seems that there is little doubt that, as a main rule, consent cannot be utilised as a basis for the processing. In practice, the lecturer who refuses will not be able to do his or her job and the student who refuses to participate in, for example, a video lecture/seminar (streaming and/or recording with student participation, either directly in video or via chat) in reality misses out on part of the education or will be the “reason” why seminars cannot be held. This means that in reality the choice is not as free as GDPR requires. Consequently, other bases for the processing must be used.
[1] See Personopplysningsloven og personvernforordningen (GDPR) med kommentarer, Jarbekk (ed.), Gyldendal 2019, p. 151.
You must provide information
The clear main rule in GDPR is that information must be given before one can collect personal data. We will provide more details later, but in brief the following applies for recording of video:
Before you start recording, you must inform those who will be included in the recording:
- That the lecture etc. will be recorded
- What it will be used for
- Who will gain access (this can be at the group level, e.g. the course students?)
- When it will be erased (if not a specific date, the criteria for erasure, e.g. after the re-sit examination for this course this semester has been held)
[Skriv tittel her]
Countless video services are available; some for streaming, some for recording and some for both. Many have their personal preference and perceive clear advantages by using precisely their preferred service.
We understand that, but unfortunately it does not help. The reason for this is that when UiT utilises video, the person data in this video are processed. This can involve employees, students or even external actors. In a video service, the personal data in the actual video and those associated with it (e.g. login, activity logs, chat, etc.) are processed.
We are subject to stringent requirements when it comes to the processing of personal data, and as a minimum we must have a data processor agreement with the supplier. Moreover, a risk assessment must be conducted. Compliance with statutory requirements is not our primary motivation for doing this. These requirements exist for a reason. It concerns safeguarding the data protection of our employees, students and guests, etc. If you use “private” video services in a teaching context, UiT cannot attend to the obligations we have. What happens if the supplier chooses to use the personal data for a completely different purpose, e.g. advertising? If the correct agreements are lacking, it is realistic that they actually have this access.
Furthermore, UiT often purchases services on other terms that those that apply for private individuals or even for a research group or unit. For several services, UiT’s terms of purchase mean that personal data is stored within the EU. However, if you go directly to the same supplier and purchase the service, you will be subject to the purely commercial terms and the data could be stored in, for instance, USA. Have you conducted a risk assessment? Do you have the necessary basis for the transfer (as required by law)?
Even if you manage to not include any personal data (it is difficult to practically impossible when using a digital service), the data you enter or generate probably has a certain value for you and for UiT? Do you know what the supplier is permitted to use these for, cf. the terms you approved when you purchased or registered yourself in the service?
Consequently, it is important that you use the services that UiT (via the Department of Information Technology) has purchased and that you use them as intended. We refer to the information under “IT services and systems – What are you permitted to use?”
UiT processes vast amounts of personal data, in many different contexts, in research, education og dissemination.
Do you plan to use personal data in research? Read more on this page (/forskning/art?dim=179056&p_document_id=604029).
It is extremely important to understand the roles various actors have in the processing of personal data.
This is necessary in order to know who has responsibility for ensuring the personal data is processed legally, who will make decisions about the processing and who those registered can contact to exercise their rights, etc.
- Who is the data controller? Does UiT have this responsibility alone or is it shared with others? Does UiT utilise data processors? What is required for this to occur in a legal way?
- Is UiT the data controller for others? What does this role involve?
- If the data is transferred overseas, what must be in place for this to be legal?
- Does UiT have external actors who perform duties for us that involve dealings with personal data although they are not a data processor?
Definitions
- racial or ethnic origin,
- political opinions,
- religious or philosophical beliefs, or
- trade union membership,
- processing of genetic data, biometric data for the purpose of uniquely identifying a natural person
- data concerning health or
- data concerning a natural person’s sex life or sexual orientation
Processing
Who is responsible?
Someone always has responsibility for the processing of personal data, a so-called “controller”. This responsibility may also be shared with others, “joint controllers”. See the menu below for further information
Controller
- Purpose: The determination of the purpose is extremely central to the processing of personal data and must be determined by the controller himself/herself - before collection of the data can commence. The purpose shall describe why it is necessary to process the relevant data, e.g. carry out admission to a programme of study, the goal of a research project, appointment of a new employee, etc.
It is important to be conscious of what the purpose is, so that the data subjects (the people the data deals with) understand what the data is used for, as well as why any subsequent further processing of the data is subject to restrictions. For instance, the data cannot be further processed in a manner that is incompatible with the original purpose(s), cf. Article 5 (1) (b).
The purpose(s) must be specified, explicit and legitimate.
- Means: The term “means” covers more than simply which technical aids shall be utilised. Central assessments and decisions related to how the personal data shall be managed are also covered, such as:
- Which data shall be processed?
- Which third parties shall have access? Which data shall be erased (and when)
- The choice of technical tools may be delegated to the processor, under certain conditions. However, the controller must ensure that the information security is safeguarded. Risk assessments cannot be conducted by the data processor alone (but they can assist)
- The controller cannot delegate assessments as mentioned in the bullet points above to the data processor.
Joint Controllers
One does not always have sole processing responsibility, as this can be shared with others, e.g. in a research project that is a joint project involving several institutions. Where two or more controllers jointly determine the purposes and means of processing, they shall be joint controllers, cf. Article 26 (1)
This is permitted providing certain requirements are fulfilled, cf. Article 26 of GDPR:
In a transparent manner, each actor (controller) shall determine their respective responsibilities for compliance with the obligations under the regulation, by means of an arrangement between them (particularly regarding the exercising of the rights of the data subjects):
- This arrangement may designate a contact point for data subjects
- The arrangement shall reflect the respective roles of the joint controllers and their relationships with the data subjects
- The essence of the arrangement shall be made available to the data subject
- Please note: Irrespective of the terms of the arrangement, the data subject may exercise his or her rights under the regulation in respect of and against each of the controllers, e.g. one of the actors has the internal responsibility for dealing with requests for access to data. The data subject may choose to send their request to one of the other controllers, who must then deal with the internal communication to process the request. The data subject cannot be rejected on the grounds that they have sent their request to the “wrong” controller.
There is no necessity for equal distribution of responsibility and decision-making authority between the various controllers. There may be different levels of “cooperation”, and different controllers may be involved in different activities/operations and at different stages of (the same) processing. As mentioned, this must be clarified in the arrangement one is responsible for stipulating pursuant to Article 26. Furthermore, it is important to be aware that the establishing of joint processing responsibilities does not give any party a “greater” right to process personal data than they would have had alone. For example, each of the parties must have a lawful basis for the processing and one party cannot simply “expand” on the lawful basis for the processing of one of the other parties.
Please be aware that it is the actual processing that is in focus and the subject of the assessment of whether there shall be joint controllers or not.
- Example: If the same personal data is the subject of processing, but each of the controllers determine their own purpose separately, it sounds more like disclosure of personal data from the original controller rather than joint processing responsibility.
Disclosure to another organization (e.g. a higher education institution)
In many instances, the transfer of personal data to external actors (enterprises, organisations, institutions, physical people) is simply the disclosure/transfer of personal data to a new controller.
When UiT has disclosed the personal data to the new controller, this person/authority is fully responsible for their processing of the personal data. We have no influence over or responsibility for how the data is processed by the external actor. Please note: If UiT still has a copy of the personal data, we are naturally still controller for our processing of these data.
For the disclosure of the personal data to be lawful, we must have a lawful basis for the processing for this disclosure. This lawful basis for the processing must comply with Article 6. If the processing involves special categories of personal data, the lawful basis for the processing must comply with Article 9. Please be aware that disclosure may involve further processing of existing data for a new purpose. In such instances, an assessment must be undertaken of whether the original purpose and the purpose of the further processing are compatible. One cannot determine a new basis for the processing (in isolation) and then the disclosure is lawful.
In instances where the disclosure is not required by law, we must assure ourselves that the recipient has a lawful basis for the processing of the data (before disclosure of the data).
Data Processor
A data processor is someone who processes personal data on behalf of the controller, cf. Article 4 (8). A data processor may be “a natural or legal person, public authority, agency or other body”, cf. Article 4 (8). Special requirements for data processors are outlined in Article 28 and 29.
The data processor must be an independent legal person or entity from the controller, e.g. employees at the controller will not be a data processor.
A data processor may be anything from a major international supplier of a cloud service (e.g. Microsoft is UiT’s data processor for our use of Office 365) to an individual (e.g. who supplies transcribing services).
There may be instances where it is not impossible that an external actor gains access to personal data when performing duties for us, but where they are not considered a data processor.
If UiT is the data processor
- We must ensure that we have entered into a data processor agreement and comply with the obligations of the agreement and Article 29.
- It is the controller’s duty to ensure that the data processor agreement is in place, but we must not receive or otherwise process personal data as a data processor before such an agreement has been signed.
- As part of the security measures, ensure that the information/data from the various controllers is kept separate from each other and from UiT’s own data.
Requirement before data processors may be utilised
Requirements for the data processor agreement
Some requirements must be fulfilled before one starts to use a data processor:
- A written data processor agreement must be entered into, cf. Article 28 (https://lovdata.no/lov/2018-06-15-38/gdpr/a28).
- There are some specific requirements concerning the content of such agreements (see below).
- You can find a template for data processor agreements here
- A risk assessment must be conducted to ensure the information security is attended to (cf. GDPR art. 32)
- This can be completely basic or extremely complicated and comprehensive, depending on the nature of the assignment/service.
- Ensure this is conducted at a sufficiently early stage to avoid the risk of entering into a binding agreement for something (e.g. for a service) that one cannot then use because the risk assessment revealed unknown risks of such a nature that they are unacceptable
- alternatively, include a “subject to approved risk assessment” clause
The data processor agreement must stipulate:
- the subject matter and duration of the processing,
- the nature and purpose of the processing,
- the type of personal data,
- categories of data subjects, and
- the obligations and rights of the controller
Furthermore, the agreement shall, in particular, stipulate that the data processor
- processes the personal data only on documented instructions from the controller, cf. Article 28 (3) (a)
- including any transfer of personal data to a third country or an international organisation
- ensures that persons authorised to process the personal data have committed themselves to confidentiality, Article 28 (3) (b)
- takes all measures required to attend to the information security (comply with Article 32, cf. Article 28 (3) (c)).
- can only enage other data processors (subcontractors) under the following conditions, cf. Article 28 (3) (d):
- the controller’s approval has been obtained. There are two methods to achieve this and the chosen method must be clarified in the agreement
- The data processor must obtain prior specific authorisation from the controller for each subcontractor, or
- The data processor receives general authorisation but must inform the controller of intended changes concerning additional/replacement subcontractors so the controller has the opportunity to object to such changes, cf. Article 28 (2)
- the data processor must impose the same binding obligations they are subject to, especially with respect to information security, cf. Article 28 (4).
- If the subcontractor fails to fulfil its data protection obligations, the data processor shall remain fully liable to the controller
- at the choice of the controller, deletes or returns all the personal data to the controller after the end of the provision of services and deletes all existing copies, cf. Article 28 (3) (g)
- makes available to the controller all information necessary to demonstrate the data processor’s compliance with the obligations, cf. Article 28 (3) (h).
- allows for and contributes to audits, cf. Article 28 (3) (h).
- including inspections, conducted by the controller or another auditor mandated by the controller
- taking into account the nature of the processing and to the extent possible
- assists the controller to fulfil its obligation to respond to requests for exercising the data subject’s rights, cf. Article 28 (3) (e)
- assists the controller in ensuring compliance with the obligations pursuant to Articles 32-36 of GDPR, cf. Article 28 (3) (f)
The above mentioned template for the data processor agreement includes all these points but must be adapted for each agreement. It cannot be signed as it is because it does not contain all the information/details required.
Sometimes the contractor may insist on using their own agreement template. This is acceptable providing it is reviewed carefully and it is concluded that the requirements of the data processor and data processor agreement are fulfilled. Please be aware that this is not always the case, even for major contractors. In such instances, one must negotiate changes of the agreement.
When is an external organization not a data processor?
Being a data processor involves processing personal data on behalf of the controller. The purpose of the agreement/assignment must, in full or in part, be to process on the controller’s behalf. If such processing is not part of the purpose of the assignment, then the contractor is not a data processor. However, a declaration of confidentiality may be necessary if there is a possibility the actor can see personal data or other confidential information. See the example declaration of confidentiality in the right-hand menu.
Some examples:
- An agreement is entered into for the repair of photocopiers. It is possible that the service technician may see personal data during the execution of his duties (e.g. on a document left in the photocopier), but this is not part of the purpose of the agreement, which is to repair the photocopier. The service technician is not a data processor even if he/she happens to see personal data.
- An agreement was entered into with a consulting firm to assist with developing a service. The consultants will perform their work on UiT’s systems, locally at UiT. No information will be transferred to their own systems. The parts of the service they will work on will not normally involve personal data. Consequently, they will not be regarded as a data processor.
- We use an external postal service to deliver letters containing personal data. The assignment is to deliver letters from A-B, not to process the personal information, and they are not a data processor.
- For more examples, see this guidance from the Danish Data Protection Agency (where some of the above-mentioned examples come from).
Please note: One cannot simply agree that someone is a controller and a data processor because it is practical or convenient. What is decisive here are the realities – who does what? Who has influence? The situation may involve joint controllers, or is in fact a disclosure/transfer of personal data to another controller.
Transfers outside the EU/EEA
Some things must be in place before personal data may be transferred overseas. Please note that this section deal with the requirements made for transferring to a given country. The requirements that must be fulfilled before one can start using a data processor or disclose personal data to another controller are also applicable, such as
- the requirements relating to a data processor agreement and risk assessment (if the recipient is a data processor)
- the requirement for a lawful basis of disclosure (if the recipient is another controller)
Please note: If the data that shall be processed is subject to special legislation that can restrict the transfer out of Norway (e.g. the Security Act), naturally this must be considered. However, this aspect is not dealt with in the information below.
Transfer to countries within the EU/EEA
Transferring personal data to recipients in countries within the EU/EEA is assimilated to transferring to an equivalent recipient in Norway. It is explicitly forbidden to restrict or prohibit the transfer of personal data to countries within the EU/EEA for reasons connected with data protection, cf. Article 1 (3).
- Please note: As mentioned, this only deals with matters related to the actual country. If, for instance, one shall start using a data processor, requirements related to information security, etc. must still be fulfilled. If this is not the case, one cannot use this data processor – and it makes no difference that it is in, for instance, France.
- What one cannot say is that a data processor must not be used because it is in France.
Transfer to countries outside the EU/EEA (“third countries”) or to international organisations
The transfer of personal data to a recipient in a country outside the EU/EEA, a so-called third country, or an international organisation, requires a lawful basis for the transfer. The transfer of personal data to third countries or international organisations is regulated by Chapter V of GDPR (Article 44 (https:/lovdata.no/lov/2018-06-15-38/gdpr/a44) - 50 (https:/lovdata.no/lov/2018-06-15-38/gdpr/a50). There are various bases for transfer, the most common of which are mentioned below. This list is not exhaustive.
- Approved third countries
EU has approved some countries that have an equivalent level of data protection within the EU/EEA. Transferring to these countries is assimilated to transferring to countries within the EU/EEA. The updated list of these approved countries is published on the EU's websites.
- EU’s Standard contractual clauses
The EU has developed a set of standard contractual clauses that may be utilised for the transfer of personal data to third countries. This contract contains several modules, and you must choose the correct one(s). The different modules regulate transfer of data from
- controller to controller
- controller to processor
- processor to processor
- processor to controller
Please note: If the recipient is a data processor, be aware that the standard contract pertaining to transfers does not replace the data processing agreement!
After the Schrems II-ruling in 2020 the transfer of data on the basis of EUs standard contractual clauses is significantly more difficult. Please be aware of this and ensure that the appropriate considerations and actions are taken before transferring any personal data, even those that might seem trivial in nature.
Resources
- Template for data processor agreement: https://anskaffelser.no/verktoy/maler-ogsa-kontrakt-og-avtalemaler/databehandleravtale-og-sjekkliste
- Checklist for data processor agreement, etc.
- With help texts (login required)
- Without help texts (login required)
- Registration form, UiT (completed, signed data processor agreements)
- Declaration of confidentiality
- Protocol of processing at UiT
- Data protection and research at UiT
- Guidance from the Norwegian Data Protection Authority
- Data processor agreement (https://www.datatilsynet.no/regelverk-og-verktoy/veiledere/databehandleravtale/)
- Basis for the processing (https://www.datatilsynet.no/regelverk-og-verktoy/veiledere/veileder-om-behandlingsgrunnlag/)
- Transfer of personal data overseas (https://www.datatilsynet.no/rettigheter-og-plikter/virksomhetenes-plikter/overfore/)
NB: Most of these documents are in Norwegian only
Privacy Policy
UiT have several different Privacy Policies, for different activities and systems. These are available in connenction to the different processing activities, but will also be gathered here.
At present time these are only available from the Norwegian website.
Here we will gather information about some key security measures.
Several measures are needed to ensure the operation and information security of UiT's infrastructure, systems, and services, which include the processing of personal data. This is for employees, students, guests at UiT, and others with connections to the university. A typical example is logging.
These can not always be informed in detail, partly because details of safety measures can be a safety risk in themselves. But we will provide the information we can provide, and which we are obliged to provide.
Logging
(information in progress)
According to the ICT regulations, any use of UiT's ICT resources can be logged, and this happens. However, it must take place under controlled conditions, and access to logs is strictly regulated. Furthermore, collection and use of logs (as well as other measures, whether it is for the maintenance of operation, security, or both) shall occur following the requirements of the privacy legislation (GDPR etc.).
The threat face UiT faces requires several security measures, not least logging. What must be logged (type of information, activity, and scope) will be more comprehensive. Still, there must be a proportionality between the intervention in the individual's privacy and the necessity and what UiT seeks to achieve.
Information about new measures that affect all users, such as Cisco Umbrella and Microsoft Defender for Endpoint, is announced via operating messages. Of other more comprehensive actions on the log page, UiT is connected to the Alert Service for digital infrastructure ("VDI"). VDI is operated by NSM and acts as a "digital burglar alarm." Some of the further details about VDI are exempt from public access, cf. § 21, and can thus not be shared, but a little more information about the service can be found here:
Notification system (VDI) - National Security Authority (nsm.no)
Multi-factor authentication
Multi-factor authentication is authentication or log in with more than one factor. This means that in addition to the username/password, an additional element is required to approve the login attempt. This is used extensively and is becoming more and more common as it is an effective and relatively simple safety measure. You are already using some form of login to browse the online bank and the Tax Administration's pages (BankID, MinID, Buypass). At UiT, we use two factors for several of our services, which will become more widespread. There are many methods to find out which password a person uses, so you can expect the password to go astray at some point. If it does, other people could log in directly to your account, but if you have a two-factor, this will be considerably more difficult.
You can use many methods, but the most common is a one-time code via SMS or an app on the phone. We will also introduce USB tokens ("hardware tokens") if you do not want or can use the app or SMS.
Every service used by employees and students at UiT, such as Office 365, SAP, Wiseflow, Canvas etc. requires multi-factor authentication.
Please see the following user guide to set up and administer multi-factor authentication:
https://uit.topdesk.net/solutions/open-knowledge-items/item/KI%201346/en_gb
VPN
VPN, Virtual Private Network, is a security mechanism that encrypts the network traffic between your PC and the services you use. This encryption is in addition to the security you get with https when you go to websites.
For technical information about UiT's VPN solution, see this support article in TopDesk.
When should I use a VPN?
VPN has two primary areas of use at UiT:
- Secure web traffic to and from your PC on unsecure networks.
- Provide access to resources that are otherwise only available by physically present at UiT's locations.
Secure web traffic to and from your PC on unsecure networks.
Here, VPN can be considered optional. This is because most services are currently secured with encryption already. This applies, for example, to all services in UiT's use of Office365, i.e. email, OneDrive and SharePoint.
However, there are cases when the use of a VPN is recommended, e.g. if you connect to unknown wireless networks or are travelling in countries outside Europe where one must take into account that state surveillance and criminal online activity is widespread.
Note: When travelling to high-risk countries such as China, Russia and Iran, one should not bring their regular work computer or mobile. Contact IT-support for more information.
Provide access to resources that are otherwise only available by physically present at UiT's locations.
The second application of VPN is mainly access to UB's journal bases. In order to directly access scientific articles through UiT's agreements, you must log in from addresses that UiT has stated as their address areas on the internet. This is described in the Help Center article above. If you go to the journals via UB's website, you don't need a VPN (there's a solution set up that bypasses the problem).
Are there any drawbacks to using a VPN?
The VPN system at UiT is set up with good capacity and should not be a bottleneck in normal use for web browsing and email. However, it can cause delays in audio and video on Teams and Zoom if you're traveling far away from Norway. This is because using a VPN sends all internet traffic to Tromsø before it goes on to the internet.
See information regarding roles and responsibilites in chapter three of the information security and privacy management system.
Privacy and information security office (FPI)
The Privacy and information security office ("FPI") is organizationally affiliated with the Department of IT, and consists of five people:
- Marte Karidatter Skadsem (CISO and leader of FPI)
- Lars Slettjord (operational security and head of CSIRT)
- Christian Isaksen (security architect)
- Elise Mengkrogen (senior legal adviser)
- Ingvild Stock-Jørgensen (senior legal adviser)
FPI works with issues of information security and privacy at an overall level, for the entire university and with questions of both digital and non-digital nature. Among other things, FPI is responsible for revising the management system for information security and privacy, managing nonconformities, carrying out control activities, writing annual reports that are submitted to the University Board, etc. More information about the assignments can be found in Chapter three of the management system.
Information security and privacy forum
The forum was created in 2019 and was originally focused on information security. In the spring of 2022, however, the mandate was expanded to include privacy/data protection.
Each unit at levels 1 and 2 has one representative, and the forum is composed of scientific and administrative staff as well as the management level. The Data Protection Officer (DPO) has the right to meet and speak.
The forum does not have decision-making authority but will serve as an advisory body for the university on issues of information security and privacy. Typically, major changes to guidelines will be submitted to the forum for input before they are finalised. Scheduled training activities of a certain size are also discussed by the forum. FPI have the main responsibility for preparing cases for the forum, but each representative has the opportunity to promote cases.
As of May 2022, the forum consists of the following representatives:
- Ingvild Stock-Jørgensen, FPI, (leader)
- Christian Isaksen, FPI (referrer)
- Anders Andersen, NT-fak
- Christine Greger, IVT-fak
- Frode Nilsen, UB
- Jan Henriksen, UMAK
- Magne Frostad, JurFak
- Sissel Eriksen, HSL
- Sølvi Brendeford Anderssen, FUF
- Terje Aspen, BFE
- Frank Mengkrogen, Helsefak.
- Eli Synnøve Foam Hanssen, ORGØK
- Nils Johan Lysnes, ITA
In addition the DPO and the CISO attend the meetings.
Data Protection Officer (DPO)
UiT has its own data protection officer who will inform and advise UiT and its employees on the obligations a resulting from the General Data Protection Regulation (GDPR) and associated legislation.
Furthermore, the DPO shall control UiT's compliance with GDPR, internal guidelines, etc. within privacy, training activities, etc.
The Data Protection Officer has an independent position and cannot be instructed in the performance of its duties.
More information about the DPO’s role and tasks can be found here.
Computer Security Incident Response Team - CSIRT
CSIRT at UiT The Arctic University of Norway
Contacts:
Lars Slettjord, Leader of CSIRT:
- +47 776 44115, normal office hours (8 am - 4:30 pm) (CET/CST)
- +47 984 02 001, critical incidents outside office hours
Ingeborg Ø. Hellemo, CSIRT:
- +47 776 44118, normal office hours (8 am - 4:30) (CET/CST)
- +47 986 68 305, critical incidents outside office hours
E-mail: csirt@uit.no
PGP: You can reach us via encrypted email. Download our PGP key here.
Please report security-related incidents involving computers or URLs belonging to UiT to the specified e-mail address above or by personal contact.
What is a security incident?
Any incident that affects information security at UiT. Events that compromise the confidentiality and integrity of data, as well as unwanted events that affect data availability.
Purpose
The group's purpose is to improve the security of UiT's computer network, reduce the number of security incidents and their damage, as well as raise awareness of security among IT consultants and end users.
CSIRT shall be the natural point of contact at UiT in connection with questions about data security and any breaches thereof.
Who CSIRT is for?
The group exists for all users connected to UiT's network (the domain uit.no and all associated domains operated or owned by UiT).
Organization
The group consists of personnel from the IT department at UiT. It is subordinate to the CIO and reports to this and the section heads. The members of the group have expertise in security, network operation and operation of various operating systems.